EasyCTF IV(2018) Writeup
Posted
Here are the Writeups for the challenges my team and I solved. The writeups will start from challenges with 30 points and up.
Haystack — 30 Points
Open the link and do a search for ‘easyctf’ and the flag would appear.
easyctf{bCbzliQHArjSEUQrzAltyILvZ
Look At Flag — 30 Points
Download the file and save it as a png. View it and you get the flag.
easyctf{FLaaaGGGGGg}
EzSteg — 30 Points
run strings [name of the file] and you will get the flag.
easyctf{l00k_at_fil3_sigS}
Intro : Reverse Engineering — 30 Points
I brute forced this challenge
hexedit — 50 Points
run strings [name of file ] | grep easyctf to get the flag.
easyctf{3921e7db}
Substitute — 50 Points
run the text through quipquip.com and get the flag.
EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS}
XOR — 50 Points
xor the first 7 chars of the cipher text with easyctf and that will give us a key of >>>>>>>.
Repeat the key to fit the length of the cipher text and get the flag.
easyctf{nqcsuwgnlxeklyafpsrexkfjx}
In Plain Sight — 70 Points
The hint for this challenge say dig around. Therefore, the dig command should probably be used.
If you have done this kind of challenges enough, you would know that the flags are normally hidden in TXT files.
Hence, running the command dig -t TXT blockingthesky.com will give you the flag.
easyctf{betcha_wish_you_could_have_used_ANY}
Adder — 80 Points
Through running the file, you should know that the program ask for 3 decimal inputs and adds them together.
This sum is then checked with a static decimal.
Disassemble the binary and you should get something like this in the main function.
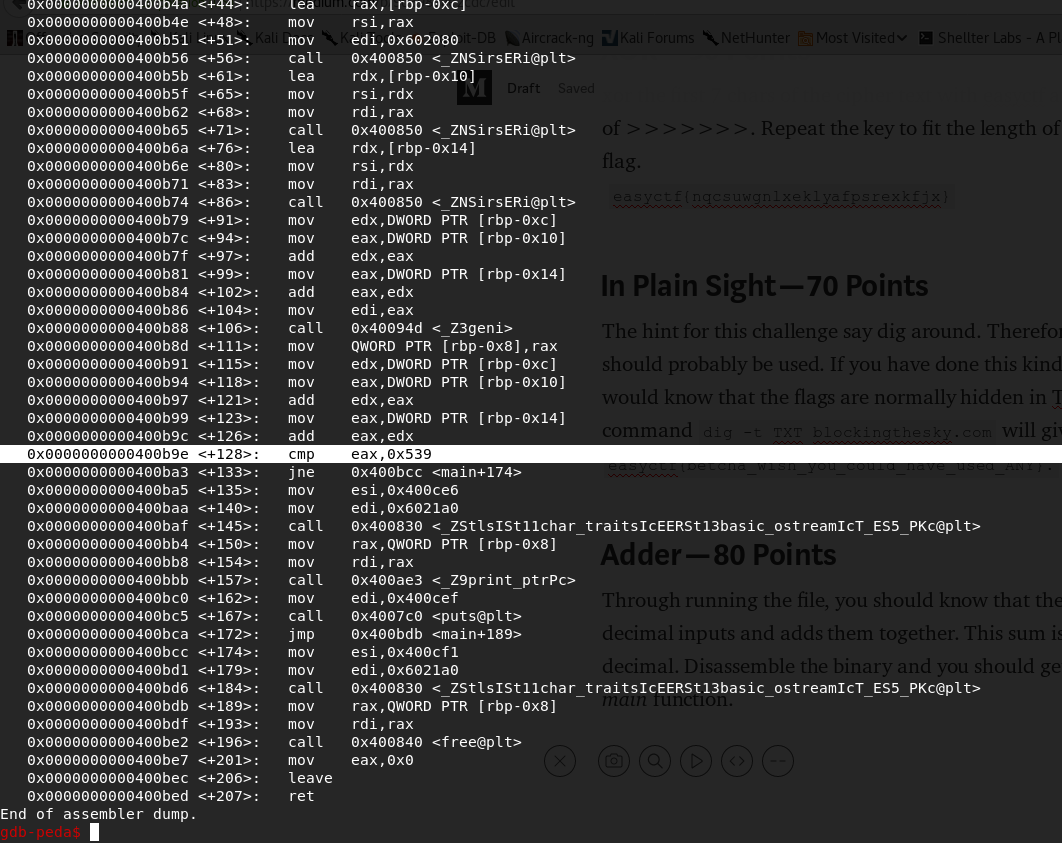
Notice that the program compares the sum of the input with 0x539 which is 1337 in decimal.
Enter any 3 numbers that add up to 1337 and get the flag.
easctf{y0u_added_thr33_nums!}
My Letter — 80 Points
This challenge presents us with a Microsoft Word document.
Most of you would have tried the flag easyctf{nevergonnagiveyouup}.
Well, So did I.
However, the solution is to extract the hidden files inside this document.
We can do this by running foremost [name of file].
That will then present us with an output folder with a zipped file in it.
Unzip the file and there is a picture named ‘template.png’. Open that picture and there is your flag.
easyctf{r3j3ct3d_4nd_d3jected}
Nosource, JR — 80 Points
Open the page and look at the page source.
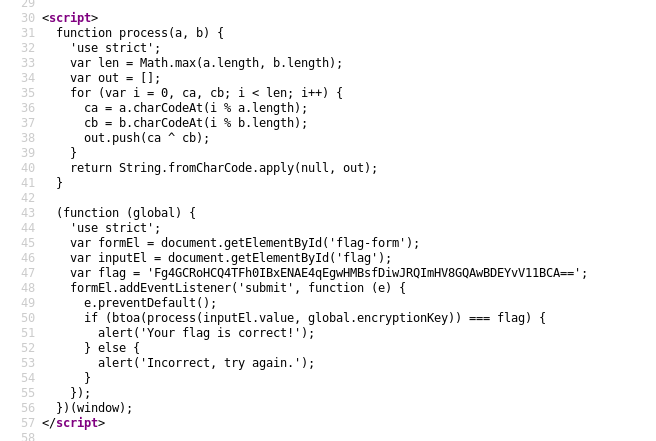
The process function looks like a xor. It takes in the flag and a key and xor them to form the encrypted flag.
So we can xor the encrypted flag with the key to decrypt it!
Run window.encryptionkey in the console to reveal the key used. The key used is “soupy”.
Now, we pass in the flag and the key into the process function to reveal the flag.
Oh wait, we need to convert the base 64 encoded flag into ascii before passing in through the function.
Run process(atob("Fg4GCRoHCQ4TFh0IBxENAE4qEgwHMBsfDiwJRQImHV8GQAwBDEYvV11GCA==","soupy")) to reveal the flag.
easyctf{congrats!_but_now_f0r_n0s0urc3_...}
Zippity — 80 Points
When you netcat into the challenge, you are greeted with this.
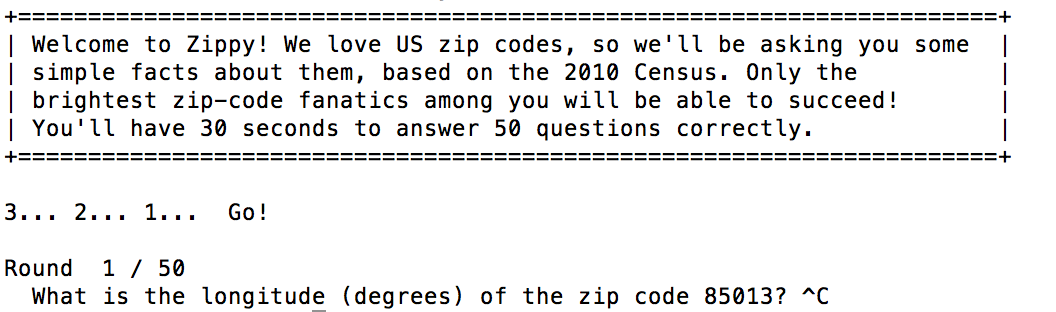
Let’s google for the relevant information.
http://proximityone.com/cen2010_zcta_dp.htm is what we arrived at.
Next, run for(i=0;i<33120;i++){console.log(obj.getCellValue(0,1) + "/" + obj.getCellValue(1,i) + "/" + obj.getCellValue(2,i) + "/" + obj.getCellValue(7,i) + "/" + obj.getCellValue(8,i))} to get the ‘database’.
Next, save the results as a text file.
Now, we need to create a script to parse the information for the challenge and send the relevant information over.
The script my team-mate created can be found at ScriptBaby
Diff — 100 Points
For this challenge, we need to compare the hex encoding of the files.
So we need to compare file2,file3 and file4 with file.
Firstly, we encode all the files into hex.
Next, use the diff command on linux to find the differences in the hex. Save this hex to form a hex string.
Convert the hex into ascii to reveal the flag.
HEX string : 656173796374667B64696666696E69746C795F616E5F657A5F70726F626C656D217D
easyctf{diffinitly_an_ez_problem!}
Digging for soup — 150 Points
Let’s run a similar command and see what we need to do.
dig -t TXT nicebowlofsoup.com
Hmmm, looks like we need to specify a NameServer. let’s try dig -t TXT nicebowlofsoup.com @153.65.43.62.
Unfortunately no flag here.
Let’s try dig -t AXFR nicebowlofsoup.com @153.65.43.62.
easyctf{why_do_i_even_have_this_domain}
Read more about AXFR here : https://en.wikipedia.org/wiki/DNS_zone_transfer