NeverLan CTF 2018
Posted

This is the writeups that my team and I solved for the NeverLan CTF 2018.
The writeups for the recon challenges will not be published as it is pure digging for information.
Have fun reading!
ajax_not_soap — 100 Points
First, let’s view the page source.
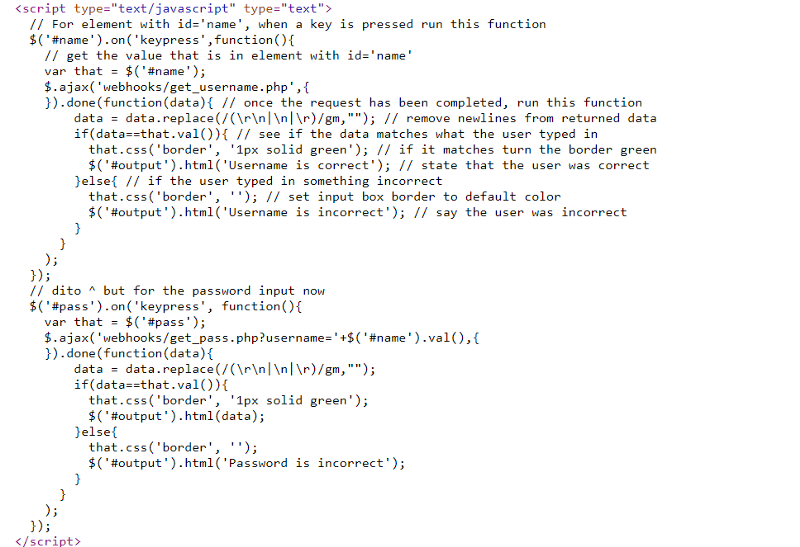
We can see that the username is compared to webhooks/get_username.php.
Upon navigation to that site, we find that the username is MrClean.
The flag can be found upon navigation to webhooks/get_pass.php?username=MrClean.
flag{hj38dsjk324nkeasd9}
the_red_or_blue_pill — 100 Points
When we enter the challenge environment, we can see 2 links : red or blue.
Upon clicking the blue, ?blue is appended to the back of the url.
Since the challenge says we can’t select both, I replaced ?blue to ?blue&red and the flag appeared.
flag{breaking_the_matrix...I_like_it!}
ajax_not_borax — 200 Points
This challenge is very similar to the other ajax challenge. This just introduces md5 hashing.
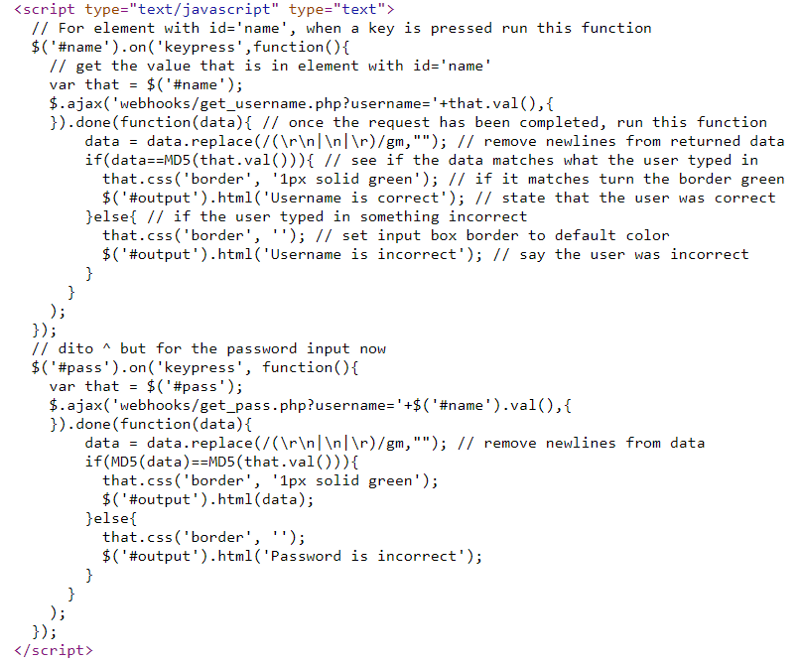
Navigate to webhooks/get_username.php?username= again to find the hashed username.
We get the MD5 hash of c5644ca91d1307779ed493c4dedfdcb7. Crack that hash to reveal the username of tideade.
Navigate to webhooks/get_pass.php?username=tideade to reveal the flag encoded with base64.
Decode that string to get the flag.
flag{sd90J0dnLKJ1ls9HJed}
Das_blog — 200 Points
Upon going to the challenge page, we see a login page.
View the page source to reveal the credentials to login with.
After that, go back to the home screen.
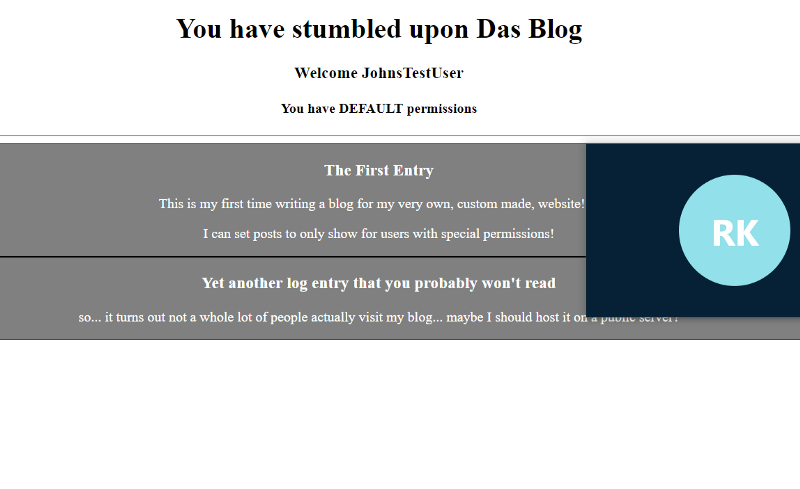
My first instinct was to change the cookies.
Using the EditThisCookie plugin, change the permission to admin and refresh the page to reveal the flag.
flag{C00ki3s_c4n_b33_ch4ng3d_?}
cookie_monster — 50 Points
Change the cookie of Red_Guy’s_name to Elmo and refresh the page to reveal the flag.
flag{C00kies_4r3_the_b3st}
Commitment Issues — 50 Points
Run strings commitment_issues | grep flag to get the flag.
flag{don't_string_me_along_man!}
Encoding != Hashing — 100 Points
Open the file in wireshark and look through the packets with HTTP Protocols.
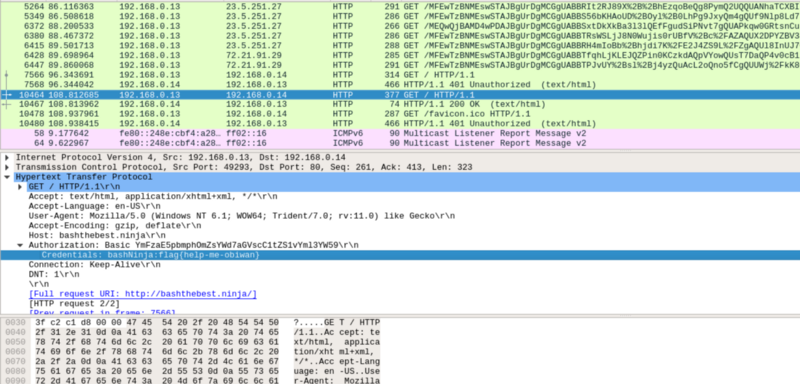
Look through the packets and find the flag in the Credentials under Authorization.
flag{help-me-obiwan}
Zip Attack — 100 Points
This challenge requires a tool called pkcrack. This tool allows you to decrypt the other files in a zip file as long as you have a copy of an encrypted file and its unencrypted version.
Run ./pkcrack -C [path to encrypted zip file] -c supersecretstuff/sw-iphone-first-order.jpg -P [path to unencrypted zip file] -p sw-iphone-first-order.jpg to get the three keys needed to decrypt the rest of the contents.
Run ./zipdecrypt <key0> <key1> <key2> [path to encrypted zip] [path to enencrypted zip]
Now, unzip the unecrypted zip to reveal flag.txt. Open the text file to reveal the flag.
flag{plaintext-attacks-are-cool!}
even more basic math with some junk — 100 Points
This challenge requires programming knowledge and we used python to solve this challenge.
We implemented regex to find all the number and add them together.
34659711530484678082 is the answer.
The script can be found at github