PragyanCTF 2018
Posted
This is the writeups for PragyanCTF 2018.
Assemble your way to the flag — 50 Points
We are presented with an ELF executable to reverse engineer. Let’s open it with radare2.
r2 -d question
Let’s look at the assembly code with pdf @ main.
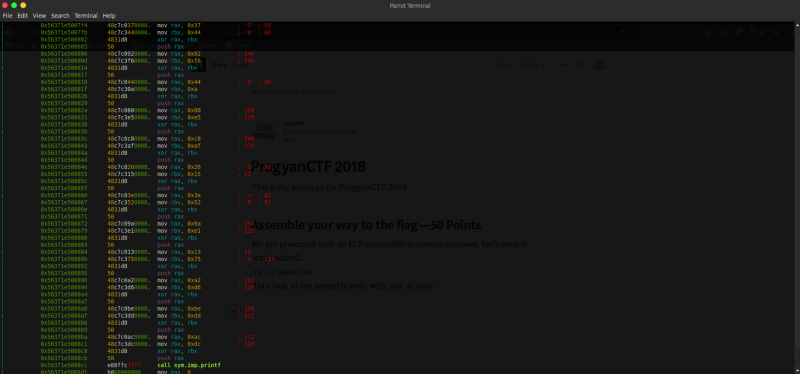
Looks like its just a repeated process of xor and pushing it into the stack.
Let’s set a breakpoint before the printf and take a look at the stack.
Set a breakpoint using db [address] and run the program using dc.
Use the command pxr@rsp to see the top of the stack.
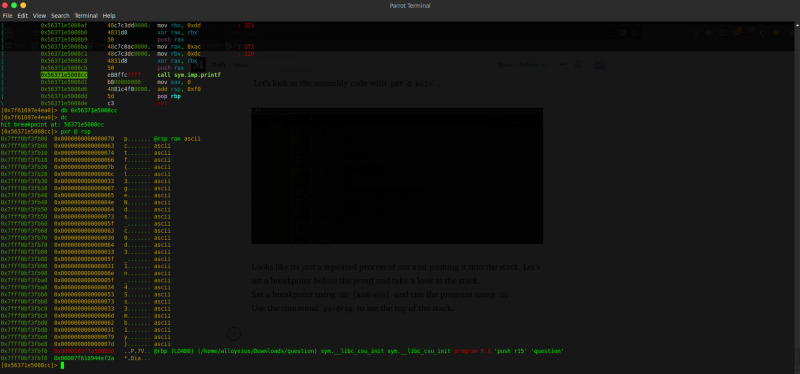
There we can see the flag.
pctf{l3geNds_c0d3_1n_4Ss3mbly}
Quick Response — 100 Points
Use an online QR Code decoder to reveal the flag.
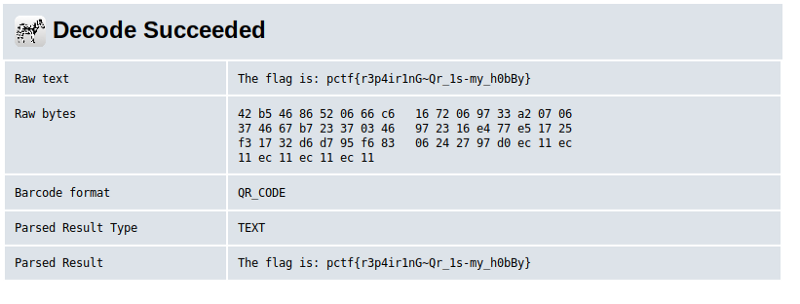
pctf{r3p4ir1nG~Qr_1s-my_h0bBy}
Xmen OR the avengers — 100 Points
Looks like it’s an XOR challenge given the name.
I wrote a script to solve this challenge.
Find the script here : Xmen Or the avengers.py
Explanation
Firstly, xor the info_clear and info_crypt to find the 1st key.
The hint of the challenge says that the second key is the MD5 hash of the 1st resulting file (the 1st key in my case).
The 1st key mentioned something about AES, ECB and Base64.
Hence, I Base64 decoded the 2nd ciphertext and decrypted it using AES (ECB) with the MD5 hash of the 1st key as the next key.
This revealed the flag. YAY
pctf{it’s_the_justice_league_DC_for_life_hellya}
Scientist’s research — 150 Points
Download the Excel Spreadsheet and zoom out. You will see the flag in reverse and mirrored.
pctf{ord3r_out_of=ch4os+this_world}
Unfinished business — 100 Points
Log into the website with the I’m Admin checked.
You should redirected to a unavailable.php.
Open the developer tools and navigate to the network tab and log in again.
This time, you should see a admin.php being recorded down. Let’s try navigating to it.
Hmmm, it’s unavailable.
Let’s try cURL-ing it. Copy the request as a cURL command and run it in your terminal.
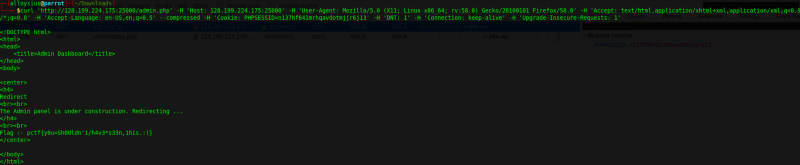
There is the flag!!
pctf{y0u=Sh0Uldn’1/h4v3*s33n,1his.:)}
Authenticate your way to admin — 150 Points
Take a look at the homepage.php they provided and you should see that the identifier should be admin in order to get the flag.
1st, log in with your team’s credentials.
Next, open another tab and login with admin/admin. You will see that the 2nd login will fail as it is not a legit account.
Now, refresh the page with your team’s account logged in.
You should see that flag now as the identifier is set to admin with the previous POST data to the server while you were logged in.
pctf{4u1h3ntic4Ti0n.4nd~4u1horiz4ti0n_diff3r}